M365 Security Audit
Benefit from reduced risks of compromise, controlled access to applications, prevention of complex threats, protection from phishing and spam, protection of confidential information.
Secure Your Business Today: Get 50% Off Our All-inclusive M365 Security Audit!
Introducing our exclusive M365 Security Audit promotion
JUST 9900 EUR for the full package!
 Safeguard your business with our comprehensive cybersecurity package, now available at an unbeatable 50% discount for a limited time only.
Safeguard your business with our comprehensive cybersecurity package, now available at an unbeatable 50% discount for a limited time only.
Today, protecting your business online is paramount. At ITP, we’re here to help you do just that. Say hello to our M365 Security Audit package – your new best friend in the digital world!
For just 9900 EUR and 1 month, you’ll get everything you need to keep your digital space safe and sound. Our all-inclusive package covers everything from user identity management to threat detection and response, ensuring your peace of mind in today’s ever-evolving digital landscape. Also, we will assist your specialists in fine-tuning important security settings. Therefore, your system will become more secure during the M365 Security Audit.
But hurry, this special offer is only around until end of June, 2024!
Now, let’s explore what’s included in our M365 Security Audit package.
Why choose ITP?
SAP Solutions
Microsoft solutions and migration to Azure
Application and infrastructure development and support
Strategic IT outsourcing
- 31+ years in the market
- Broad partner ecosystem with 40+ vendors and partners
- Proven use of best practices and innovative technologies, confirmed by key vendors
- Team with extensive experience in complex IT projects for leading companies, including
- Development of a global SAP template and its subsequent rollout to group companies
- Migration to S/4HANA
- Setup and migration of infrastructure to Azure
- Competence center and specialists certified by SAP and Microsoft
Start a project with us!
Let's Do This!
Detailed description of Included Services
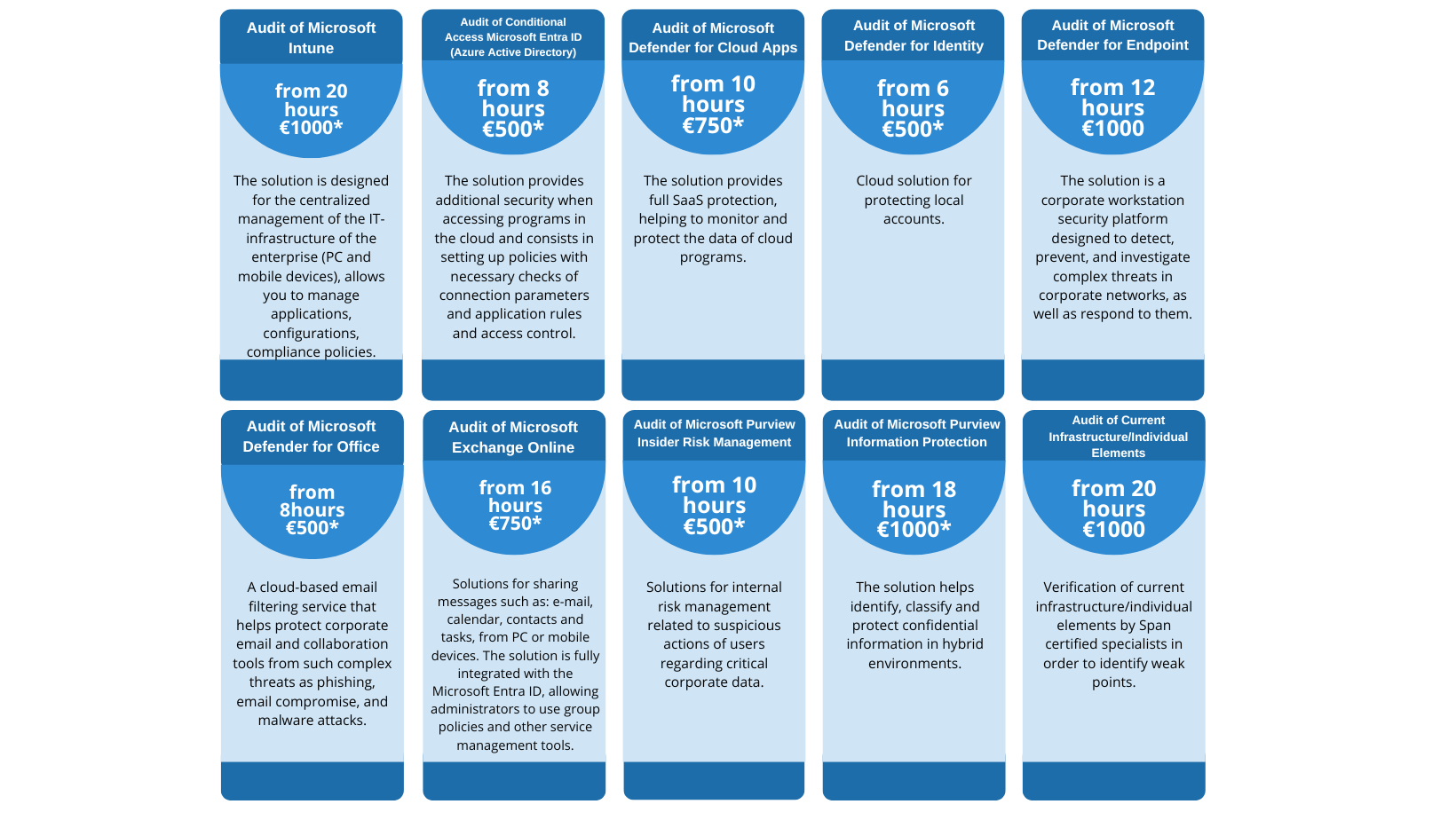
Conditional Access Microsoft Entra ID (Azure Active Directory):
The solution provides additional security when accessing programs in the cloud and consists in setting up policies with necessary checks of connection parameters and application rules and access control.
The service includes:
- Setting such basic policies as: ban legacy authentication; MFA for administrative accounts and users; access to corporate applications exclusively from devices that meet the requirements; protection of applications for mobile devices.
- Conducting an online training session for employees of the IT department on the features of using the solution (2 years).
Result:
- Reducing the risk of compromise of accounts
- Controlled access to applications
Microsoft Intune:
The solution is designed for the centralized management of the IT-infrastructure of the enterprise (PC and mobile devices), allows you to manage applications, configurations, compliance policies.
The service includes:
- Configuring the mobile application management scenario (MAM) for Android and iOS (test group up to 5 devices)
- Processing of basic mobile device management scenarios (MDM)
- Adding and adapting a test group of Windows 10/11 domain PCs (up to 5 PCs) to the Microsoft Intune service (Hybrid Azure AD Joined Scenario)
- Conducting an online training session for employees of the IT department on the features of using the solution (2 years).
Result:
Safe access to corporate applications/data for employees who use BYOD (Android and iOS) or corporate devices (Android, iOS, Windows).
Microsoft Defender for Cloud Apps
The solution provides full SaaS protection, helping to monitor and protect the data of cloud programs.
The service includes:
- Setting such basic policies as: policy of activity of users (Activity Policy); policy for monitoring new applications (Discovery New App Policy); session policy of users (Session Policy); file policy (File Policy);
- Conducting an online training session for employees of the IT department on the features of using the solution (2 years).
Result:
Effective monitoring of the use of cloud services.
Microsoft Defender for Identity
Cloud solution for protecting local accounts.
The service includes:
- Installation of Microsoft Defender for Identity sensors on Active Directory domain controllers (up to 3 controllers);
- Configuring Active Directory (creating accounts, auditing policies) for the service robot;
- Conducting an online training session for employees of the IT department on the features of using the solution (1 year).
Result:
Detection of compromised accounts and suspicious activities within the on-premises Active Directory infrastructure.
Microsoft Defender for Endpoint
The solution is a corporate workstation security platform designed to detect, prevent, and investigate complex threats in corporate networks, as well as respond to them.
The service includes:
- Configuring the Microsoft Defender for Endpoint service;
- Connection, adaptation and configuration of up to 10 devices with OS Windows 10/11;
- Demonstration of robots from endpoints using cloud tools;
- Conducting an online training session for employees of the IT department on the features of using the solution (2 years).
Result:
Control of infrastructure, prevention of complex threats, notification from a single unified platform.
Microsoft Defender for Office
A cloud-based email filtering service that helps protect corporate email and collaboration tools from such complex threats as phishing, email compromise, and malware attacks.
The service includes:
- Setting such basic policies as: safe links; safe investments; anti-phishing; antispam; protection from malicious programs;
- Conducting an online training session for employees of the IT department on the features of using the solution (2 years).
Result:
Protection of e-mail and Microsoft Teams from phishing, spam and dangerous content messages.
Microsoft Exchange Online
Solutions for sharing messages such as: e-mail, calendar, contacts and tasks, from PC or mobile devices. The solution is fully integrated with the Microsoft Entra ID, allowing administrators to use group policies and other service management tools.
The service includes:
- Consultations and implementation of Exchange Hybrid and the process of migration of mailboxes to the cloud;
- Conducting an online training session for employees of the IT department on the features of using the solution (2 years).
Result:
Coexistence of terrestrial and cloud mail services and the possibility of operative transfer of mailboxes between terrestrial and cloud infrastructures.
Microsoft Purview Insider Risk Management
Solutions for internal risk management related to suspicious actions of users regarding critical corporate data.
The service includes:
- Consulting regarding the use of the Insider Risk Management tool;
- Pilot launch of the process of monitoring suspicious activity of users;
- Conducting an online training session for employees of the IT department on the features of using the solution (2 years).
Result:
Detection of suspicious actions of users against corporate data.
Microsoft Purview Information Protection
The solution helps identify, classify and protect confidential information in hybrid environments.
The service includes:
- Consultation regarding the use of Microsoft Information Protection tools;
- Preparation of a set of types of detection of confidential data (up to 5 types);
- Preparation of a DLP policy (1 policy) to prevent leakage of confidential information;
- Preparation of confidentiality markings for data classification (up to 5 markings);
- Preparation of a policy of automatic marking of data (1 policy);
- Conducting an online training session for employees of the IT department on the features of using the solution (2 years).
Result:
Classification and protection of confidential corporate information.
Audit Current Infrastructure/Individual Elements
Verification of current infrastructure/individual elements by Span certified specialists in order to identify weak points.
The service includes one option to choose from:
- Assessment of cloud infrastructure Microsoft Azure;
- Assessment of hybrid infrastructure Microsoft Azure;
- Rating of the hybrid infrastructure Microsoft 365;
- Rating of the current level of information security Microsoft:
- authentication and authorization of users;
- level of protection of critical corporate data;
- security level of corporate services and applications;
- level of security of corporate network and equipment.
Result:
A report containing objective information and expert recommendations on cost optimization, risk assessment and infrastructure improvement.
Conclusion
Don’t miss out on this opportunity to safeguard your business at an incredible discount.
Contact us now to schedule your free consultation and secure your spot by taking advantage of this limited-time offer.
This exclusive offer won’t last forever, it is valid until June 2024, and promotions like this are rare – we only release them once a year.
You can reach out via email, phone, or through our contact form below.